Verifying Signed Binary
Signed Binary
All binary files made available by us are also signed (.sig file). That is, there are two files: the binary and the signature file. This method improves security, as the origin of that file can be trusted and guarantees the file's integrity. To verify the source of the file, first, you need to download Vitro code signing certificate:
curl -o sign_ca.crt "https://cloud.3mdeb.com/index.php/s/dGdXC8ZyPmmj8ok/download"
cURL is a program that allows you and the server to transfer data among each other. In this case, we are downloading a file.
The first thing you should do is inspect the certificate to see if it is valid. You can do that by going to the Inspecting the Certificate section. If the certificate is fine, now you need to extract the public key:
openssl x509 -in sign_ca.crt -pubkey -noout > vitro_code_signing.pubkeyIf you trust the certificate, you can now verify all downloaded binaries if they are trustworthy or not. The command is:
$ openssl dgst -sha256 -verify vitro_code_signing.pubkey -signature <signature_file>.sig <binary_file>For example, consider you download the SDK binary and want to verify it using its signature file. The first step is to download it:
curl -o shard-sdk.a "https://cloud.3mdeb.com/index.php/s/e4cCgADpjrTQkcY/download"
curl -o shard-sdk.a.sig "https://cloud.3mdeb.com/index.php/s/JALgKH33JS5izHq/download"After the download is finished, just run the following command to check its signature:
$ openssl dgst -sha256 -verify vitro_code_signing.pubkey -signature shard-sdk.a.sig shard-sdk.aThe output, hopefully, will be:
Verified OKInspecting the Certificate
You can inspect the certificate on the command-line by using the openssl tool. On Ubuntu, Windows, and macOS, it is also possible to double click on the .crt file to open it.
openssl x509 -text -noout -in sign_ca.crtThere are four main fields that you must pay attention to:
- Issuer
Issuer: C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert SHA2 Assured ID Code Signing CAHere we can check that the certificate was issued by DigiCert.
- Validity
Validity
Not Before: May 20 00:00:00 2021 GMT
Not After : Mar 8 23:59:59 2022 GMTIn this field, we can verify if the certificate is still valid or not. In this case, it is until March 8, 2022.
- Subject
Subject: C = US, ST = Texas, L = Austin, O = Vitro Technology Corporation, CN = Vitro Technology CorporationThe same information can be obtained if you double click the certificate, as shown below:
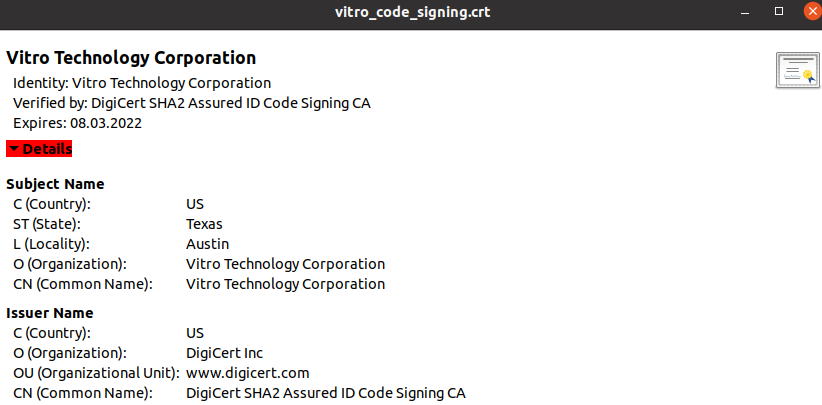
Ubuntu's certification information page.
Finally, the subject shows that the certificate was issued for Vitro Technology Corporation.
You can also check the certificate by using certificate decoders online. An example is the one from GoDaddy. You should open the sign_ca.crt file in a text editor and paste the content to the decoder window. For example, the content to copy and paste is:
-----BEGIN CERTIFICATE-----
MIIFPjCCBCagAwIBAgIQB3nnB32Z/xMsivsOYaqC/DANBgkqhkiG9w0BAQsFADBy
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMTEwLwYDVQQDEyhEaWdpQ2VydCBTSEEyIEFzc3VyZWQg
SUQgQ29kZSBTaWduaW5nIENBMB4XDTIxMDUyMDAwMDAwMFoXDTIyMDMwODIzNTk1
OVowfDELMAkGA1UEBhMCVVMxDjAMBgNVBAgTBVRleGFzMQ8wDQYDVQQHEwZBdXN0
aW4xJTAjBgNVBAoTHFZpdHJvIFRlY2hub2xvZ3kgQ29ycG9yYXRpb24xJTAjBgNV
BAMTHFZpdHJvIFRlY2hub2xvZ3kgQ29ycG9yYXRpb24wggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQDHVHA6f1+58UFl7Ex1bi7EjldD5Dc/aj0kq8kyulUB
0lU1VaCosjddU0KvhAd7BvTeXTdrmyrI14QB2o9VeMx0JSgHUzDvkiwYyps/bR/Z
Aw+SYqsEGHGK3c57agW5WS370TZZj0s/aGikJncg81Bkgw9CgYyIK3pfq+enA+aj
VuFuoffCkymbup8/7vrav1F+lC+2aw1f/9LrZSfWb6kSVkxCZ1GuGqLiz2bnAD72
2zwpRtSrLFrNPp5yIhfV6uFUy7oHDoBWSv+SqbkjrCk3bJTcDDP+7aGEXFwwqdkb
6dJDLVlvAd5LtH+HNshBagMSbaJ0580qoJanTEEY9iGZAgMBAAGjggHEMIIBwDAf
BgNVHSMEGDAWgBRaxLl7KgqjpepxA8Bg+S32ZXUOWDAdBgNVHQ4EFgQU2wsSsL05
OocP9xlLrqD6Rn/pEoAwDgYDVR0PAQH/BAQDAgeAMBMGA1UdJQQMMAoGCCsGAQUF
BwMDMHcGA1UdHwRwMG4wNaAzoDGGL2h0dHA6Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9z
aGEyLWFzc3VyZWQtY3MtZzEuY3JsMDWgM6Axhi9odHRwOi8vY3JsNC5kaWdpY2Vy
dC5jb20vc2hhMi1hc3N1cmVkLWNzLWcxLmNybDBLBgNVHSAERDBCMDYGCWCGSAGG
/WwDATApMCcGCCsGAQUFBwIBFhtodHRwOi8vd3d3LmRpZ2ljZXJ0LmNvbS9DUFMw
CAYGZ4EMAQQBMIGEBggrBgEFBQcBAQR4MHYwJAYIKwYBBQUHMAGGGGh0dHA6Ly9v
Y3NwLmRpZ2ljZXJ0LmNvbTBOBggrBgEFBQcwAoZCaHR0cDovL2NhY2VydHMuZGln
aWNlcnQuY29tL0RpZ2lDZXJ0U0hBMkFzc3VyZWRJRENvZGVTaWduaW5nQ0EuY3J0
MAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcNAQELBQADggEBANou2X121336+wnwfwUB
Bz/un0d1Z+g5FbjY1KQQ44JcZURwf/T6QZwIvrC8zmIlx8Md+3CvGUJhuvDknLub
zaC0ju8yrTQKrKwLu8FF7fj7A1t1IsstK7hrfnwWVR61E5EyxsBtvuGRE3ztcp7r
45w9S3tQ8uEOw9dnHCrpaaSxWvwx66ydyNOubVIBgujuAft7921PX9JM3ttaSMM/
uKDPHNOUJuMLZ+FotYVhpdz59UMGVfgXvUCcoFZUsbwg3l4LHf/+8V5OVil0QgnW
FYPdrEp5MQc2SCottcq8lmAjMTafsp5nnrGX4dLJI8Og4Ilh6Lzd0B6YHbwgXYEF
lcs=
-----END CERTIFICATE-----This will result in the following:
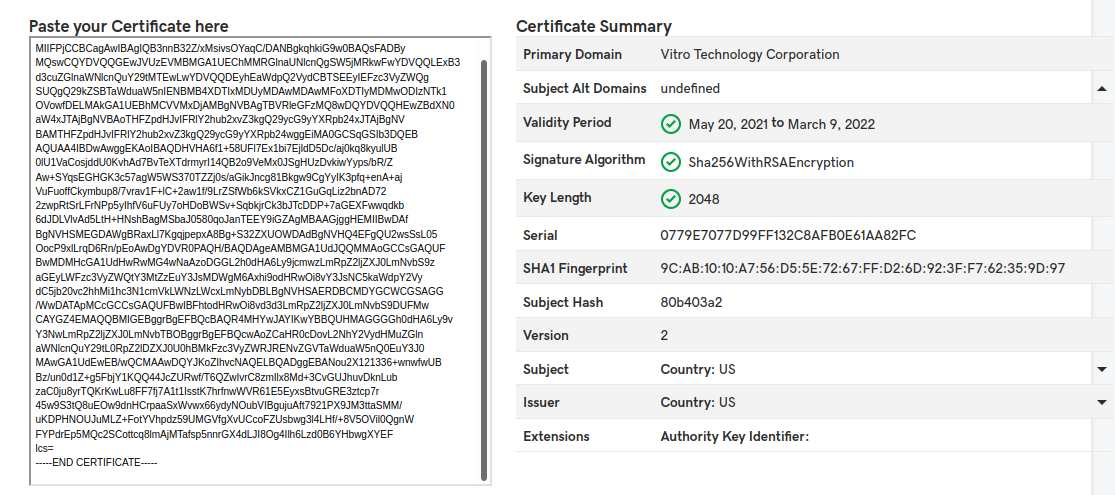
GoDaddy's certification information page.
Updated 9 months ago
